Over the last 6 months, I’ve been blessed with various pharma hacks on almost all my site.
(http://agilefaqs.com, http://agileindia.org, http://sdtconf.com, http://freesetglobal.com, http://agilecoachcamp.org, to name a few.)
This is one of the most clever hacks I’ve seen. As a normal user, if you visit the site, you won’t see any difference. Except when search engine bots visit the page, the page shows up with a whole bunch of spammy links, either at the top of the page or in the footer. Sample below:
Image may be NSFW.
Clik here to view.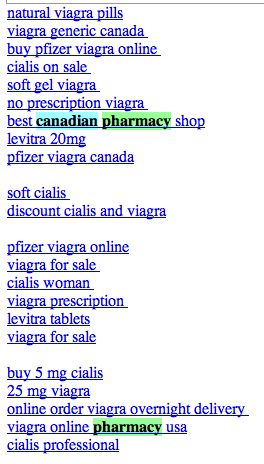
Clearly the hacker is after search engine ranking via backlinks. But in the process suddenly you’ve become a major pharma pimp.
There are many interesting things about this hack:
- 1. It affects all php sites. WordPress tops the list. Others like CMS Made Simple and TikiWiki are also attacked by this hack.
- 2. If you search for pharma keywords on your server (both files and database) you won’t find anything. The spammy content is first encoded with MIME base64 and then deflated using gzdeflate. And at run time the content is eval’ed in PHP.
This is how the hacked PHP code looks like:
Image may be NSFW.
Clik here to view.
If you inflate and decode this code it looks like:
Image may be NSFW.
Clik here to view.
Image may be NSFW.
Clik here to view.
Image may be NSFW.
Clik here to view.
- 3. Well documented and mostly self descriptive code.
- 4. Different PHP frameworks have been hacked using slightly different approach:
- In WordPress, the hackers created a new file called wp-login.php inside the wp-includes folder containing some spammy code. They then modified the wp-config.php file to include(‘wp-includes/wp-login.php’). Inside the wp-login.php code they further include actually spammy links from a folder inside wp-content/themes/mytheme/images/out/’.$dir’
- In TikiWiki, the hackers modified the /lib/structures/structlib.php to directly include the spammy code
- In CMS Made Simple, the hackers created a new file called modules/mod-last_visitor.php to directly include the spammy code.
Again the interesting part here is, when you do ls -al you see:-rwxr-xr-x 1 username groupname 1551 2008-07-10 06:46 mod-last_tracker_items.php
-rwxr-xr-x 1 username groupname 44357 1969-12-31 16:00 mod-last_visitor.php
-rwxr-xr-x 1 username groupname 668 2008-03-30 13:06 mod-last_visitors.php
In case of WordPress the newly created file had the same time stamp as the rest of the files in that folder
How do you find out if your site is hacked?
- 1. After searching for your site in Google, check if the Cached version of your site contains anything unexpected.
Image may be NSFW.
Clik here to view.
- 2. Using User Agent Switcher, a Firefox extension, you can view your site as it appears to Search Engine bot. Again look for anything suspicious.
Image may be NSFW.
Clik here to view.
- 3. Set up Google Alerts on your site to get notification when something you don’t expect to show up on your site, shows up.
Image may be NSFW.
Clik here to view.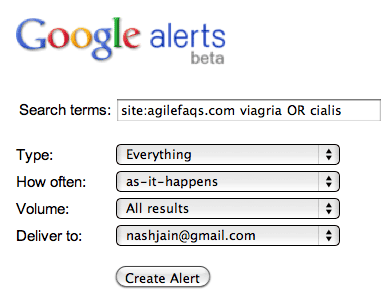
- 4. Set up a cron job on your server to run the following commands at the top-level web directory every night and email you the results:
- mysqldump your_db into a file and run
- find . | xargs grep “eval(gzinflate(base64_decode(“
If the grep command finds a match, take the encoded content and check what it means using the following site: http://www.tareeinternet.com/scripts/decrypt.php
If it looks suspicious, clean up the file and all its references.
Also there are many other blogs explaining similar, but different attacks:
- Check Your Sites With Google
- WebShell Hack – An Update
- Understanding and cleaning the Pharma hack on WordPress
- WordPress Exploit: We Been Hit By Hidden Spam Link Injection
- Spam Link Injection Hacked (and How I Hopefully Fixed It)
- Google Cloaking Hack Targeting WordPress & How to Fix It
- How to Diagnose and Remove the WordPress Pharma Hack
Hope you don’t have to deal with this mess.